How To Secure Apache with Let's Encrypt on Ubuntu 20.04 (ok)
https://www.digitalocean.com/community/tutorials/how-to-secure-apache-with-let-s-encrypt-on-ubuntu-20-04
Last updated
https://www.digitalocean.com/community/tutorials/how-to-secure-apache-with-let-s-encrypt-on-ubuntu-20-04
Last updated
Chú ý: Giải quyết bài toán sau khi đăng ký đề chuyền về dạng https giờ tôi không muốn thì làm thế nào???
ApacheLet's EncryptUbuntu 20.04
By Erika HeidiPublished onApril 29, 2020 88.7kviews
English Deutsch Español Français Bahasa Indonesia 日本語 Português РусскийEnglish
Not using Ubuntu 20.04? Choose a different version or distribution.
Ubuntu 20.04CentOS 8CentOS 7Debian 9Debian 8Debian 10Ubuntu 18.04Ubuntu 16.04Ubuntu 14.04Ubuntu 20.04
Let’s Encrypt is a Certificate Authority (CA) that facilitates obtaining and installing free TLS/SSL certificates, thereby enabling encrypted HTTPS on web servers. It simplifies the process by providing a software client, Certbot, that attempts to automate most (if not all) of the required steps. Currently, the entire process of obtaining and installing a certificate is fully automated on both Apache and Nginx.
In this guide, we’ll use Certbot to obtain a free SSL certificate for Apache on Ubuntu 20.04, and make sure this certificate is set up to renew automatically.
This tutorial uses a separate virtual host file instead of Apache’s default configuration file for setting up the website that will be secured by Let’s Encrypt. We recommend creating new Apache virtual host files for each domain hosted in a server, because it helps to avoid common mistakes and maintains the default configuration files as a fallback setup.
To follow this tutorial, you will need:
One Ubuntu 20.04 server set up by following this initial server setup for Ubuntu 20.04 tutorial, including a sudo non-root user and a firewall.
Both of the following DNS records set up for your server. You can follow this introduction to DigitalOcean DNS for details on how to add them.
An A record with your_domain pointing to your server’s public IP address.
An A record with www.your_domain pointing to your server’s public IP address.
Apache installed by following How To Install Apache on Ubuntu 20.04. Be sure that you have a virtual host file for your domain. This tutorial will use /etc/apache2/sites-available/your_domain.conf as an example.
In order to obtain an SSL certificate with Let’s Encrypt, we’ll first need to install the Certbot software on your server. We’ll use the default Ubuntu package repositories for that.
We need two packages: certbot, and python3-certbot-apache. The latter is a plugin that integrates Certbot with Apache, making it possible to automate obtaining a certificate and configuring HTTPS within your web server with a single command.
Copy
You will be prompted to confirm the installation by pressing Y, then ENTER.
Certbot is now installed on your server. In the next step, we’ll verify Apache’s configuration to make sure your virtual host is set appropriately. This will ensure that the certbot client script will be able to detect your domains and reconfigure your web server to use your newly generated SSL certificate automatically.
In order to be able to automatically obtain and configure SSL for your web server, Certbot needs to find the correct virtual host within your Apache configuration files. Your server domain name(s) will be retrieved from the ServerName and ServerAlias directives defined within your VirtualHost configuration block.
If you followed the virtual host setup step in the Apache installation tutorial, you should have a VirtualHost block set up for your domain at /etc/apache2/sites-available/your_domain.conf with the ServerName and also the ServerAlias directives already set appropriately.
To check this up, open the virtual host file for your domain using nano or your preferred text editor:
Copy
Find the existing ServerName and ServerAlias lines. They should look like this:/etc/apache2/sites-available/your_domain.conf
Copy
If you already have your ServerName and ServerAlias set up like this, you can exit your text editor and move on to the next step. If you’re using nano, you can exit by typing CTRL+X, then Y and ENTER to confirm.
If your current virtual host configuration doesn’t match the example, update it accordingly. When you’re done, save the file and quit the editor. Then, run the following command to validate your changes:
Copy
You should get a Syntax OK as a response. If you get an error, reopen the virtual host file and check for any typos or missing characters. Once your configuration file’s syntax is correct, reload Apache so that the changes take effect:
Copy
With these changes, Certbot will be able to find the correct VirtualHost block and update it.
Next, we’ll update the firewall to allow HTTPS traffic.
If you have the UFW firewall enabled, as recommended by the prerequisite guides, you’ll need to adjust the settings to allow HTTPS traffic. Upon installation, Apache registers a few different UFW application profiles. We can leverage the Apache Full profile to allow both HTTP and HTTPS traffic on your server.
To verify what kind of traffic is currently allowed on your server, you can use:
Copy
If you have followed one of our Apache installation guides, your output should look something like this, meaning that only HTTP traffic on port 80 is currently allowed:
To additionally let in HTTPS traffic, allow the “Apache Full” profile and delete the redundant “Apache” profile:
Copy
Your status will now look like this:
Copy
You are now ready to run Certbot and obtain your certificates.
Certbot provides a variety of ways to obtain SSL certificates through plugins. The Apache plugin will take care of reconfiguring Apache and reloading the configuration whenever necessary. To use this plugin, type the following:
Copy
This script will prompt you to answer a series of questions in order to configure your SSL certificate. First, it will ask you for a valid e-mail address. This email will be used for renewal notifications and security notices:
After providing a valid e-mail address, hit ENTER to proceed to the next step. You will then be prompted to confirm if you agree to Let’s Encrypt terms of service. You can confirm by pressing A and then ENTER:
Next, you’ll be asked if you would like to share your email with the Electronic Frontier Foundation to receive news and other information. If you do not want to subscribe to their content, type N. Otherwise, type Y. Then, hit ENTER to proceed to the next step.
The next step will prompt you to inform Certbot of which domains you’d like to activate HTTPS for. The listed domain names are automatically obtained from your Apache virtual host configuration, that’s why it’s important to make sure you have the correct ServerName and ServerAlias settings configured in your virtual host. If you’d like to enable HTTPS for all listed domain names (recommended), you can leave the prompt blank and hit ENTER to proceed. Otherwise, select the domains you want to enable HTTPS for by listing each appropriate number, separated by commas and/ or spaces, then hit ENTER.
You’ll see output like this:
Next, you’ll be prompted to select whether or not you want HTTP traffic redirected to HTTPS. In practice, that means when someone visits your website through unencrypted channels (HTTP), they will be automatically redirected to the HTTPS address of your website. Choose 2 to enable the redirection, or 1 if you want to keep both HTTP and HTTPS as separate methods of accessing your website.
After this step, Certbot’s configuration is finished, and you will be presented with the final remarks about your new certificate, where to locate the generated files, and how to test your configuration using an external tool that analyzes your certificate’s authenticity:
Your certificate is now installed and loaded into Apache’s configuration. Try reloading your website using https:// and notice your browser’s security indicator. It should point out that your site is properly secured, typically by including a lock icon in the address bar.
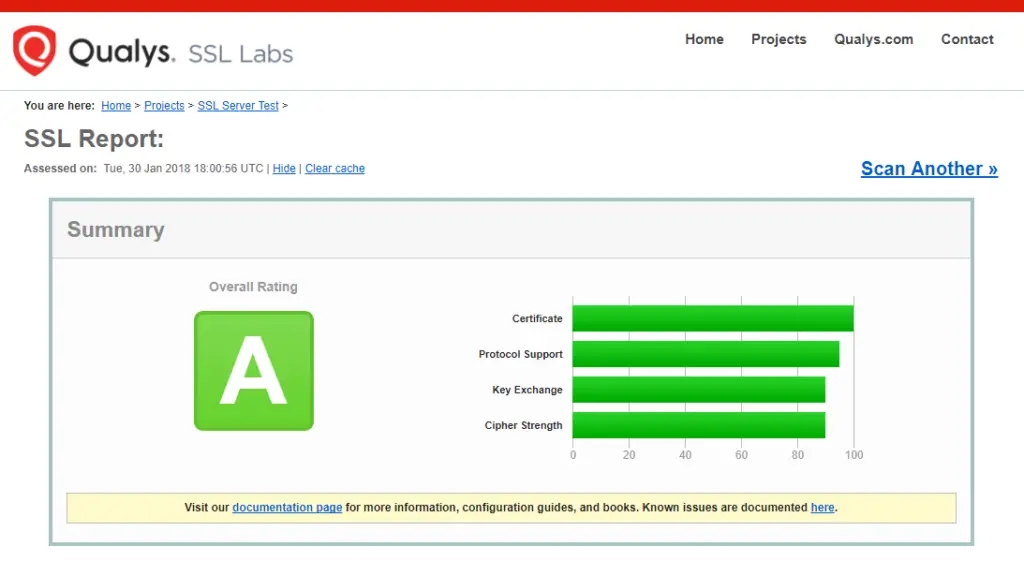
You can use the SSL Labs Server Test to verify your certificate’s grade and obtain detailed information about it, from the perspective of an external service.
In the next and final step, we’ll test the auto-renewal feature of Certbot, which guarantees that your certificate will be renewed automatically before the expiration date.
Let’s Encrypt’s certificates are only valid for ninety days. This is to encourage users to automate their certificate renewal process, as well as to ensure that misused certificates or stolen keys will expire sooner rather than later.
The certbot package we installed takes care of renewals by including a renew script to /etc/cron.d, which is managed by a systemctl service called certbot.timer. This script runs twice a day and will automatically renew any certificate that’s within thirty days of expiration.
To check the status of this service and make sure it’s active and running, you can use:
Copy
You’ll get output similar to this:
To test the renewal process, you can do a dry run with certbot:
Copy
If you see no errors, you’re all set. When necessary, Certbot will renew your certificates and reload Apache to pick up the changes. If the automated renewal process ever fails, Let’s Encrypt will send a message to the email you specified, warning you when your certificate is about to expire.
I like to write and build stuff. Passionate about community and open source <3
Still looking for an answer?
Ask a questionSearch for more help
Comments
16 Comments
B
I
UL
OL
Link
Code
Highlight
Table
The original Ubuntu 20.04 package have this bugs it did not install the right python3-certbot-nginx
So the only solution for ubuntu (AMD64) are via snap
sudo snap install certbot --beta --classic
or
2.
Thanks to Andreas for making his PPA available temporarily to fixed the problem
I hope this will help people who want to upgrade to 20.04Reply Report
Step 3 /etc/apache2/sites-available/your_domain.conf
… ServerName yourdomain ServerAlias www.yourdomain …
do I need to change the name like this if my domain name is examplesite
/etc/apache2/sites-available/examplesite.conf
… ServerName examplesite ServerAlias www.examplesite …Reply Report
0vincentgong7 October 19, 2020
No. You should do:
… ServerName yourdomain.com ServerAlias www.yourdomain.com …edited by MattIPv4Reply Report
Hi, thanks for your guide.
One question, can I follow this guide with a subdomain? So that I don’t have to purchase and maintain another domain name?
Im trying to increase the security of the access of phpmyadmin of my server.
I didn’t follow this tutorial, but the certbot program can create any sub-domain certificate for you. I have obtained many sub-domain certificates for my sites with the certbot. So I believe that you can achieve the same result by following this tutorial carefully. As it said in the tutorial “make sure you have the correct ServerName and ServerAlias settings configured in your virtual host.”Reply Report
:~# sudo certbot –apache Bootstrapping dependencies for Debian-based OSes… (you can skip this with –no-bootstrap) Ign:1 http://ppa.launchpad.net/certbot/certbot/ubuntu focal InRelease Hit:2 http://archive.ubuntu.com/ubuntu focal InRelease Err:3 http://ppa.launchpad.net/certbot/certbot/ubuntu focal Release 404 Not Found [IP: 2001:67c:1560:8008::15 80] Hit:4 https://repos.insights.digitalocean.com/apt/do-agent main InRelease Get:5 http://mirrors.digitalocean.com/ubuntu focal InRelease [265 kB] Hit:6 http://mirrors.digitalocean.com/ubuntu focal-updates InRelease Hit:7 http://mirrors.digitalocean.com/ubuntu focal-backports InRelease Hit:8 http://security.ubuntu.com/ubuntu focal-security InRelease Reading package lists… Done E: The repository ’http://ppa.launchpad.net/certbot/certbot/ubuntu focal Release’ does not have a Release file. N: Updating from such a repository can’t be done securely, and is therefore disabled by default. N: See apt-secure(8) manpage for repository creation and user configuration details. apt-get update hit problems but continuing anyway… Reading package lists… Done Building dependency tree Reading state information… Done Note, selecting ‘python-is-python2’ instead of 'python’ Note, selecting 'python-dev-is-python2’ instead of 'python-dev’ Package python-virtualenv is not available, but is referred to by another package. This may mean that the package is missing, has been obsoleted, or is only available from another source
E: Package 'python-virtualenv’ has no installation candidateReply Report
0erhanpaker1 December 14, 2020
Hi, How do I remove Let’s Encrypt ssl. I installed wordpress ssl but I want to delete it.?
Đọc thêm: https://devanswers.co/lets-encrypt-ssl-apache-ubuntu-18-04/
Last updated on April 27th, 2020
Let’s Encrypt is a certificate authority that provides free SSL certificates that are just as secure as current paid certificates. In this guide we will configure an SSL certificate for Apache on Ubuntu 18.04.
You should be using a non-root user with sudo privileges as explained in Ubuntu 18.04 / 19.10 Initial Server Setup.
You should also have Apache already installed and serving web pages before continuing with this guide. Please see Installing Apache on Ubuntu 18.04 / 19.10.
Cloudflare Users: Note that you may not need Let’s Encrypt and can instead use Cloudflare’s own shared Universal SSL certificate and an Origin CA. If you want to keep Cloudflare and also use Let’s Encrypt, you must Pause Cloudflare now, otherwise it will interfere with certificate deployment. Once the Let’s Encrypt cert is deployed, you must unpause and set SSL to Full (Strict) in the Cloudflare crypto settings, otherwise you may get a redirect loop error. Be warned that when Let’s Encrypt tries to auto renew after 90 days, it will fail if you have Cloudflare enabled.
Let’s begin by updating the package lists and installing software-properties-common. Commands separated by && will run in succession.
Now add the repositories universe and certbot.
Press ENTER if prompted.
Update the package lists again and install certbot for Apache. This is the Let’s Encrypt client.
Press y and ENTER when prompted to continue.
We will now obtain a cert for our test domain example.com. Certbot has an Apache plugin, which automates the certificate installation.
Enter an email address where you can be contacted in case of urgent renewal and security notices.
Press a and ENTER to agree to the Terms of Service.
Press n and ENTER to not share your email address with EFF.
If you have multiple domains already configured on your server, you will see a list of them here. In this example, we only have one domain example.com and its www. prefix.
Select option 1 if you don’t want to use the www. prefix in your website address, otherwise select option 2.
Press 2 and ENTER to redirect all traffic to HTTPS.
You’re done!
You can now go to ssllabs.com/ssltest/ and run an SSL test on your domain.
A successful test should receive an A rating.
As Let’s Encrypt certs expire after 90 days, they need to be checked for renewal periodically. Certbot will automatically run twice a day and renew any certificate that is within thirty days of expiration.
To test that this renewal process is working correctly, you can run:
Please ensure your Cloudflare SSL settings are correct. Log in to Cloudflare, go to Crypto and make sure SSL is set to Full (Strict).
Be warned that when Let’s Encrypt tries to auto renew after 90 days, it will fail if you have Cloudflare enabled.
Let me know if this helped. Follow me on Twitter, Facebook and YouTube, or 
p.s. I increased my AdSense revenue by 68% using AI 
In this tutorial, you’ve installed the Let’s Encrypt client certbot, configured and installed an SSL certificate for your domain, and confirmed that Certbot’s automatic renewal service is active within systemctl. If you have further questions about using Certbot, their documentation is a good place to start.Was this helpful?YesNo 16Report an issueAbout the authorsErika Heidi
4.94 (18 votes)